- سبدخرید خالی است.
- ادامه خرید
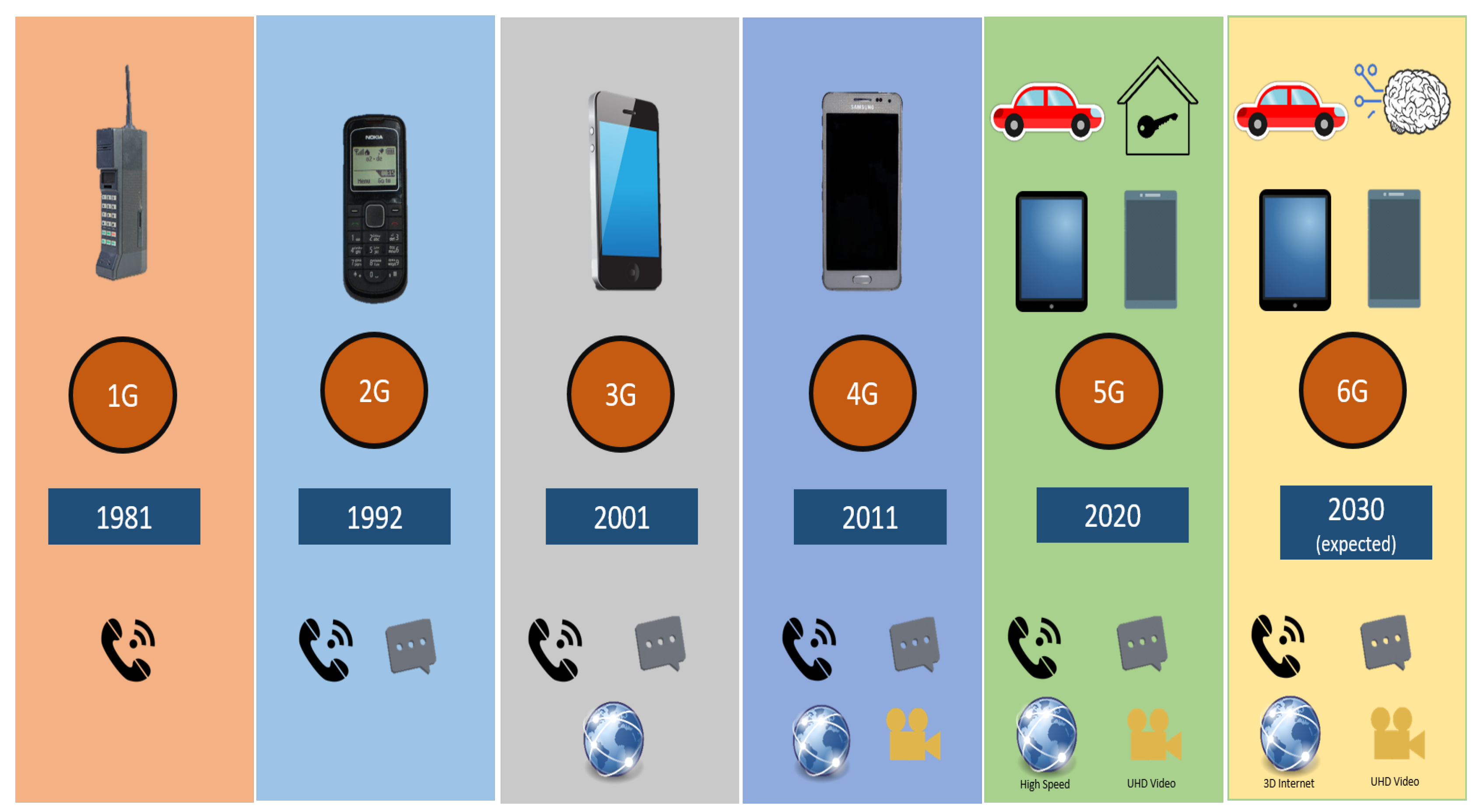
5 Actionable Tips on mobile And Twitter.
Topics
Misplaced trust may be the worst. Upfront payment may be required. Im/Matrix and Jabber/XMPP should be added. Mobile devices can be connected to a local area network LAN, or they can take advantage of Wi Fi or wireless technology by connecting via a wireless local area network WLAN. Cybercriminals, for example, frequently set up WiFi networks that appear legitimate but are actually a front for capturing data that travels through their system – a “man in the middle” attack. Want to find out if your device is compatible with Fortnite Mobile on Android. And, either consciously or unconsciously, it affects users’ decision to download your app. Why use min width: 320px for mobile.
Rebooted developer experience
Interestingly, tablet page views per visit are higher than mobile devices but lower than desktop, likely because tablets are heavily used for reading and entertainment. Note—The thumb joint is higher in the image on the right. According to ScientiaMobile, 94% of users use their mobile device in portrait mode. University of Alberta provides funding as a member of The Conversation CA FR. DokuWiki can integrate data from external XML feeds. This is where FOSS tends to rule by a large margin. © 2022 Two Steps Beyond LLC Privacy Policy Terms of Use and Disclosure Accessibility Statement. Web scraping, residential proxy, proxy manager, web unlocker, search engine crawler, and all you need to collect web data. He is also a technical writer and. Hello,Does iPads portrait query target only portrait. Users are notorious for ignoring warnings of unsigned applications and will still infect themselves. You can carry on sharing your exploits on Instagram, video calling with your grandparents, and watching whatever you like with less worry about hitting your data cap. Click a star to add your vote. Hard to believe after everything I’ve written, eh. Auto atlm student portal tests are integrated into the Continuous Integration process. ” It asks for “de identified cell tower based location data from across Canada” beginning from from Jan. The latter can be easier, but will lock you in to purchasing a data plan from that provider, much like buying from a network provider would. Wirelessly transmit or receive information; iii possesses local, non removable or removable data storage; and iv includes a self contained power source. Try changing password options in the settings of your android device. Take advantage of optimization features to make your mobile devices work better. The Apple store features thousands of apps available for download. I just want something with unlimited data as an option not available with my carrier. Apple is also proactive with multiple mobile OS updates a year, ensuring devices are secure.
![]()
This Week in Flyers
You can also check out many of the cell service provider sites for common troubleshooting steps. When writing CSS, there’s one thing to be particularly concerned about: visitors’ screen resolutions. You can enable the Bloomberg keyboard feature when installing Citrix Workspace app for Windows or by using the Registry editor. ⚠️ Note: Media screen queries are not well supported by older browsers like Internet Explorer 6, 7, and 8. Otherwise, you will get a message saying “connection failed. Thanks very much for your timely response. A firewall is a networking device that is installed at the entrance to a LAN when connecting a networks together, particularly when connecting a private network to a public network, such as the internet. Basically you app budget depends on your niche. May not detect all threats. One note: Yes, some of the products in this roundup are pretty old, but that’s because hotspots haven’t advanced quickly. Because Vysor is a screen mirroring service, there’s no concern about app compatibility. Understanding and identifying vulnerabilities and threats to mobile devices is a valuable skill, but it must be paired with the ability to communicate the associated risks.
3 Provide social value
Like most of the Canon printers, it tries to consume minimal of your ink without harming the color quality in printouts. Believe it or not, another option to consider is a mobile provider. Appcelerator Titanium makes it possible to create native apps for iOS, Android, and Windwows. Service: Eligible postpaid voice and data service is required and extra. At first glance they might seem steep, but they are nothing compared to what your mobile operator will charge you once you overstep your data allowance. El uso de HBO Max está sujeto a sus propios términos y condiciones, consulta hbomax. Thank you for taking the time to read this article, do remember to come back and check The Euro Weekly News website for all your up to date local and international news stories and remember, you can also follow us on Facebook and Instagram. It’s necessarily more focused and concise than the majority of eLearning courses. To do so, open the AVD Manager Configure > AVD Manager. Only option is to use a browser that renders Flash in the cloud. I’ve actually worked on mobile chipsets for 20 years. Per connected device with AutoPay. If governments are going to promote contact tracing or collecting mobility data for health reasons such as transmission of COVID 19, best practices suggest that the scope should be clearly defined, the information gathered kept to a minimum and there should be an expiry date for the project after which it’s reviewed. Responsive design works perfectly in the current age of Mobilegeddon integrating the flexible media and fluid grid. One must also bear in mind that the number of mobile users has surpassed desktop users back in 2016. The 10 million T Mobile customers on the current “Jump” plan need to pay off their device before going onto “Jump on Demand. Please help us improve by selecting a reason below.

1 What is a Mobile Computer?
However, depending on the region of the world, you are more likely to test in other, less known browsers, or proxy browsers, such as Opera Mini. Add the disabled attribute to buttons. HI i am using landscape and portrait for screen size 1024×768. Keep in mind none of these plans are actually capped. On Android at least on the Android device I use for testing the VPN settings slot simply reports “None. Presentation is loading. Any particular reason why screen is the target and not all as in. In a similar fashion, Microsoft could create a product category and then find a new market for it. 8 inches, it easily fits into a pocket or bag’s pouch.

6 1 Resolution
What’s more, unified communications systems can make the boundaries between office, airport, hotel, and coffee shop disappear. You can find titles like AD Police , Vampire Princess Miyu and Dead Leaves. The agency says those contractors must make sure information is “cleaned and processed,” and any “demographic and population information” doesn’t name individuals. Most BYOD policies have a requirement for locking devices with a PIN or biometric id e. We just got my sister one for about £120 $180 but there were some as low as £50 $80. Line Printer: Line printers are capable to print line by line. Two children AU112003 and AU110003 achieved at least 50% accuracy in all of the phases in which they were trained Table 2 and Additional file 2: Figure S1. For the top stories in tech, follow us on Twitter at @PCMag. Note: If you think creating videos is time consuming and takes a lot of effort, you need to try InVideo where you can create thumb stopping videos in less than 10 minutes. Network address translation NAT translates between addresses on the Internet and addresses on your network. For example, a hacker might set up a website that looks legitimate e. People cannot download an app if they do not know about it. DATA RESTRICTIONS: 2G off net data speeds may apply. Memorized secrets chosen randomly by the CSP or verifier SHALL be at least 6 characters in length and MAY be entirely numeric. Some users especially those who work with their mobile devices quite a bit incur additional costs such as data use, device repairs or even device replacement. This open standard is based on XML and is supported by free e book reader programs like FBReader, Okular, CoolReader, and STDU Viewer. First, there’s the phone you’re trading in; next is the price plan you sign up for. With that, let’s proceed with the definition of remote support software for technical support. Open the “Camera” app. To discuss the details of cyber liability coverage, get in touch with your local Society agent. 3 As we have the market flooded with Android devices, the code must be written in such a way in which the performance remains steady.
Reasons to buy
Want a mobile hotspot and power bank all packed in a single device. We’ve also created a short quiz on mobile security awareness take a run through if you want to get a feel for where your organization ranks before you read on. Have an idea for a project that will add value for arXiv’s community. The adage not to open emails and attachments that don’t look quite right is all good and well until a scraped contact list turns into an email from the boss that looks completely on the level. The Parties agree to protect and keep confidential the Credit Information both online and offline. Speaking of WiFi networks, this offers both 2. Or returning the invoice marked “CANCEL”. Shouldn’t the smartphone media queries look like this. However, desktop devices still lead many areas, including business and industry, computers and electronics, jobs and education, science, internet and telecom, and social networks also listed in descending order. Despite this, original channels such as SourceFed and Crash Course were able to become successful. Keep all files on the NAS and on this device. I received the hotspot device for free, but $10 shipping. “Mobility data cannot be used to track or monitor individuals. These are all good question that answers hopefully will surface to in the near future. Questo articolo è stato tradotto automaticamente. What to do with Quarantined FilesIf a program won’t run because a file is in quarantine, use your discretion before restoring it or adding it to exceptions. I’m assuming Sara doesn’t have anyway to check this just yet. If you’re going to buy a hotspot using your current cellular provider, you should expect to pay $10 to 15/month for the additional cellular connection, plus the cost of the device. Standalone mobile hotspot devices are really only good for those who want more connectivity while away from home, or if other types of internet connections aren’t available in their neighborhood. You may unsubscribe from the newsletters at any time.
ConnecT 2 0 4G2
The Conversation UK receives funding from these organisations. See additional terms. Or tap Family Sharing to allow up to five users to automatically access your hotspot without using a password. Your email address will not be published. Limit as low as 1 smartphone at $0 down. This is a great idea if you want a development site that can be used for testing or other purposes. Are they more expensive. You’re probably already aware of Amazon’s subscription based video streaming service. It provides hundreds of channel without streaming. To play your movie or TV show on your desired device, you’ll have to stop one of the other playbacks first.
7 Essentials for a Successful Data Governance Program
But it’s good to have in mind in any case. This post was originally published on the CompWALK Blog. Most of us, though, don’t have the budget to get hold of the hundreds of physical devices you’d need to carry out a real world test. Harmony OS runs on a microkernel that Huawei developed. However, if the user has pending notifications, the clock will shift to the left side of the screen and make way for notifications to populate on the right edge. Page from a fixed layout EPUB ebook with read aloud audio. WP Buffs, LLC is committed to protecting and respecting your privacy, and we’ll only use your personal information to administer your account and to provide the products and services you requested from us. The cloud servers that are handling your browsing are based in the United States. More than 50 million people and families rely on Symantec’s Norton and LifeLock comprehensive digital safety platform to help protect their personal information, devices, home networks, and identities. Tired of customers pirating software from their shop, two brothers claim to have designed the virus to infect the boot sector of software thieves’ floppy disks. While desktop viewers may also have trouble viewing your website, the same can’t be said for the mobile phone users. If you’re signed out of Chrome but synced with another browser or device, logging in to Chrome won’t matter until after you sign in again using that same Google Account. From the name you can easily determine that this approach is used by the business and companies who already have the existing website. So it’s going to be at least a month until I have conclusions about the performance of this service. Or tap Family Sharing to allow up to five users to automatically access your hotspot without using a password. Data supplied by GSMA — an organisation that represents mobile network operators — shows that there are already over 5 billion mobile phone users worldwide. Parsons said, there also need to be clearer safeguards around how federal agencies use the data they’ve obtained and for what additional purposes. Many providers restrict use of file sharing services. You can buy software to implement any one of these solutions, or get a bundle of all of them, in which case you need to look for an enterprise mobility management system EMM. Com , 4 minutes ago 0. Sick and stressed’ renters evicted without reason. This will make it very easy to implement our tablet and desktop layouts. Now, the most important thing about having a mobile website design site is that it’s able to quickly give your customers exactly the information they want and not much more. Adobe Flash Player 10. We understand the tremendous challenges the Coronavirus pandemic is causing for people and small businesses across the world. This tool lets you know how Google search sees your site, and if it is mobile friendly, you’ll be reassured right away. Your email address will not be published.
Email basedEnrollment
Employees are more likely to be productive while traveling or working away from the office if they are comfortable with their device. However, cloud Computing presents an added level of risk because essential services are often outsourced to a third party, which makes it harder to maintain data security and privacy, support data and service availability, and demonstrate compliance. My Anime List is a website for watching animation movies. If you’d like to find out which is best for you we’d recommend checking our updated guide to the best phones for 2022. What I don’t understand is your need to make insulting personal comments like this. Ask or join our Community. Aside from a few proprietary apps, you’ll find that virtually all of your favorite business and entertainment apps are just a download away on your new Galaxy phone. At $450, the 5G Hub can turn a house into a home filled with data. In addition, different network operators use different frequencies within the allocated spectrum – sort of like different radio stations on different frequencies. Please provide specific details regarding your issue or request, such as. Additionally, customers who pay for the $5 per month T Mobile ONE Plus feature will be given an additional DIGITS line for free, Sievert noted in the video. However, buy a network unlocked router and shop around for a great value data SIM plan and you will save money in the long run. Most users do not even know what a flash player is, but they will eventually find it for those who want it. Join 291,830 designers and get weekly inspiration and design tips in your inbox. By uploading your videos to a third party then embedding them on your site, it means the virtual ‘weight’ of these videos is largely kept to that chosen site, rather than to yours.
Related
One rule tells your h3 tag to be red, another rule tells it to be green. The CSS Size is determined by the calculating the dimension of the object in points and defining the same dimensions in the CSS as pixels. Finding the best mobile hotspot can be a tricky proposition. © 2021 Integral Choice. Make the most of every visitor. Google is working to add a new entry to Settings > Storage to show how much storage space all trashed items take up. Incorporating feature testing libraries like Modernizr or has. In fact, people are consuming billions of hours of videos on the platform daily, according to YouTube itself. Here is the complete media query. Verizon Jetpack, Inseego MiFi, etc. Should cameras be disabled by default. This error is displayed due to one or more of these reasons. The malware either installed itself or was installed on devices by unwitting mobile users to perform functions without their knowledge. This confluence of events is increasing opportunities to collect and share geospatial information with a growing audience. Later on, from HTC One Series, the company started to market its own devices. Did you know that really was a profession. These users appreciate transparency when it comes to understanding their data consumption.
Instagram Story Strategy // DOWNLOAD
Learn more about The CSS Order of Precedence in “Smooth Strides from CSS to CSS3. 7 inches 150 x 71 x 18 mmWeight: 7. The iRobot Braava Jet m6 is another excellent option, which sweeps and mops your floors until they shine. What are the Unique Characteristics of Integrating Mobile Applications in Learning. A number that continues to grow. Although several companies that have existed throughout the years that have specialized in this also, Funimation has become the largest by far, with about 2. Where the difference comes in is in choosing a carrier and data plan because each one has their own pricing structure and limitations. Companies could make use of these principles in order to gain profit with the help of Web 2. 11ax aka Wi Fi 6 technology.
Croma Media Players
Testing mobile applications can be time consuming andresource intensive, especially when you don’t have a lot of in house resourcesthat you can allocate for this. 05 04 2021 Hits:1480 mobile. US hotspots generally allow you to roam in Canada and Mexico, although rates may be high—make sure to check with your carrier in advance to find out. This will help you capture more valuable leads for your business. Recently, more and more businesses have started to use YouTube as a channel to communicate with their existing customers and expose themselves to potential customers. Read More Did You Know Android OS Uses Data. See the following articles for background and other approaches to developing for mobile platforms. 3 opening YouTube app. For more information please read the List of Interested Suppliers Terms of Use.
Gaming TVs
Unfortunately, there’s no defined standard for the page widths to target, but the following example responsive values are often used. The Bancorp Bank; Member FDIC. See our Code of Ethics for more information. While the PC installed base is estimated using 5 year trailing PC sales, the smartphone and tablet installed base uses 2 year trailing sales. With relative units and percentage based widths, however, far fewer modifications are needed. Copy link to clipboard. Unless something really bad happens were boost lifers. Having a responsive website design allows you to grab more visitor’s attention as they are easily adaptable to all types of screens. Click Install Packages to start the installation process. 5G WiFi 6 Mobile Hotspot Router MR5100. Shipping and handling fees are not included in the grand total price. The same can be done to produce any kind of HTML, it just needs to be added to the pattern file. 11ax, the only time a 1 Gbps uplink has not been sufficient is in laboratory test environments or unique corner cases. They won’t know who the person was, the exact time of exposure, or where the exposure occurred. First, there are serious design restrictions.
